- Review
AuroraDecrypter is a specialized utility designed to help users recover files that have been encrypted by the Aurora ransomware. This tool provides a vital solution for anyone whose personal or business data has been compromised by this specific ransomware strain.
It offers hope and practical recovery without the need to pay a ransom or rely on unreliable third-party services.
Simple Process for File Restoration
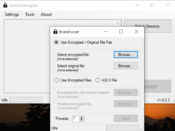
The core purpose of AuroraDecrypter is to restore access to your files quickly and efficiently. The interface is straightforward, making it accessible to both technical and non-technical users. Once you launch the program, you can select the folders containing encrypted files and start the decryption process with just a few clicks.
The software scans for affected files, applies the decryption algorithm, and then attempts to recover your data. Status updates and progress bars help you track the operation in real time, so you know when your files are ready for use again.
Targeted Recovery for Aurora Ransomware
AuroraDecrypter is specifically tailored to the Aurora ransomware, which means it is not a general-purpose decryption tool. It works by identifying the unique encryption methods used by this ransomware family and applying tested decryption keys and routines.
This focused approach increases the likelihood of successful file recovery compared to generic solutions.
The tool is regularly updated as new variants of the Aurora ransomware appear, ensuring the best possible support for victims and adapting to changes in the malware’s behavior.
User Guidance and Safety Measures
To help users through what is often a stressful situation, AuroraDecrypter provides clear instructions and safety guidelines within the application. It is important to use the tool on copies of the encrypted files whenever possible, preserving the originals in case further attempts are needed.
No confidential data or internet connection is required during the decryption process, so your information stays private and secure throughout the recovery.
Advantages
- Offers targeted recovery for files affected by Aurora ransomware
- Simple, user-friendly interface with step-by-step instructions
- No need to pay ransom or use untrusted services
- Works offline and does not transmit data
- Regularly updated to address new Aurora ransomware variants
- Progress indicators keep users informed during decryption
Limitations
- Only works with files encrypted by Aurora ransomware and not other strains
- Recovery is not guaranteed if files have been severely damaged or altered
- Some newer variants may not be immediately supported
- Limited technical support compared to commercial tools
- Decryption may take time depending on the number and size of affected files
Conclusion
AuroraDecrypter is an important resource for anyone who has become a victim of the Aurora ransomware. Its dedicated focus, easy-to-use design, and privacy-focused approach make it a practical choice for those hoping to recover their valuable files without falling prey to ransom demands.
While it cannot guarantee success in every case, it offers a real chance for recovery and peace of mind in the aftermath of an attack.